Private CA: Own your PKI and Digital Trust
- Molntek
- Application , Data , Security , Software , Technology
- November 1, 2024
Table of Contents
Digital communication relies on trust, but that trust is often outsourced to public Certificate Authorities. A private Certificate Authority offers a fundamentally different approach: complete control over how digital identities are created, validated, and managed.
Instead of accepting pre-defined trust boundaries, you define exactly who and what can be authenticated in your digital ecosystem.
This article explain why you should consider running your own Certificate Authority.
Every time you connect to a secure website, your browser verifies the site’s identity using digital certificates issued by Certificate Authorities. These CAs act as trusted third parties, essentially vouching for the authenticity of the websites you visit. But what if your security requirements go beyond what public CAs can offer?
Why a Private CA?
Complete Control Over Trust
When you operate your own CA, you maintain full control over:
- Who gets certificates
- What types of certificates are issued
- How long certificates remain valid
- The exact validation process for certificate requests
Enhanced Security
By running your own CA, you:
- Eliminate dependence on external certificate providers
- Reduce the attack surface by keeping all certificate operations in-house
- Maintain a clear chain of custody for all certificates
- Can immediately revoke compromised certificates
- Mitigate risks of certificate authorities being compromised or coerced
Threat Mitigation
A private CA helps protect against various security threats, including:
- Rogue certificates issued by compromised public CAs
- Unauthorized access to sensitive internal systems
- Man-in-the-middle attacks targeting your organization
- Eavesdropping on confidential communications
Cost-Effectiveness
For organizations that need many certificates for internal services, running a private CA can be more economical than purchasing certificates from commercial providers, especially when considering:
- Internal development environments
- Machine-to-machine communications
- IoT device authentication
- Internal services and applications
Hybrid Approaches
While a private CA offers significant benefits, it’s not always feasible or necessary to completely replace public CAs. Many organizations opt for a hybrid approach, where they:
- Use public CAs for external-facing services and websites
- Operate a private CA for internal systems, sensitive communications, and critical infrastructure
This hybrid model allows organizations to leverage the trust and scalability of public CAs while maintaining control over their most sensitive digital assets.
Real-World Applications
Consider these scenarios where a private CA proves invaluable:
- Healthcare Organizations
- Securing patient data transmission between internal systems
- Authenticating medical devices on the network
- Ensuring compliance with health data protection regulations
- Financial Institutions
- Securing internal banking applications
- Authenticating automated trading systems
- Protecting sensitive financial transactions
- Government Agencies
- Maintaining classified communication channels
- Securing inter-department data exchange
- Managing access to sensitive resources
Implementation Considerations
While running a private CA offers significant benefits, it also comes with responsibilities:
Security Requirements
- Secure key storage (preferably using Hardware Security Modules)
- Strict access controls to CA management systems
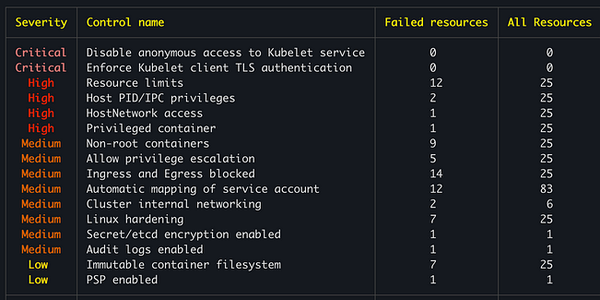
- Regular security audits and monitoring
- Robust backup and recovery procedures
Operational Needs
- Certificate lifecycle management
- Regular maintenance and updates
- Staff training and documentation
- Integration with existing systems
Best Practices
To maximize the benefits of your private CA:
- Establish Clear Policies
- Define certificate issuance criteria
- Document validation procedures
- Set certificate lifetime policies
- Create emergency revocation procedures
- Implement Strong Controls
- Use multi-factor authentication for CA access
- Maintain detailed audit logs
- Regular security assessments
- Automated certificate monitoring
- Plan for Scale
- Design for future growth
- Automate routine tasks
- Implement self-service where appropriate
- Maintain redundancy for critical components
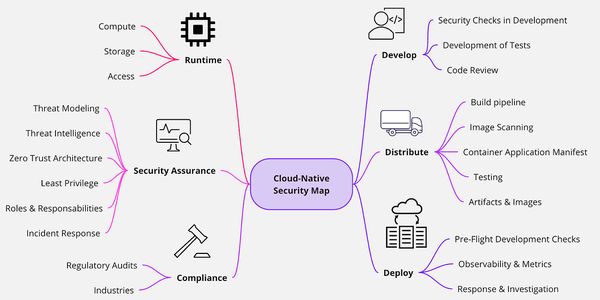
The Solution: Cloud-Native Private Certificate Authority
Traditional certificate management has long been a complex, error-prone process involving significant manual intervention, complex infrastructure, and substantial operational overhead.
Cloud-native Private CAs fundamentally transform this landscape, offering unprecedented security, scalability, and efficiency.
Here are the main technological advantages:
1. Uncompromising Security
By leveraging Cloud Providers’ state of the art resources, such as AWS KMS with FIPS 140-2 Level 3 certified hardware, private Cloud CA ensures that private keys are stored in the most secure environment possible.
This level of protection goes beyond traditional on-premises solutions, providing a hardened security boundary that protects the most critical component of any Public Key Infrastructure (PKI) - the root and issuing CA private keys.
2. Serverless Architecture
A 100% serverless infrastructure eliminates traditional operational burdens:
- Zero server maintenance
- Automatic scaling
- Minimal security update requirements
- Reduced attack surface
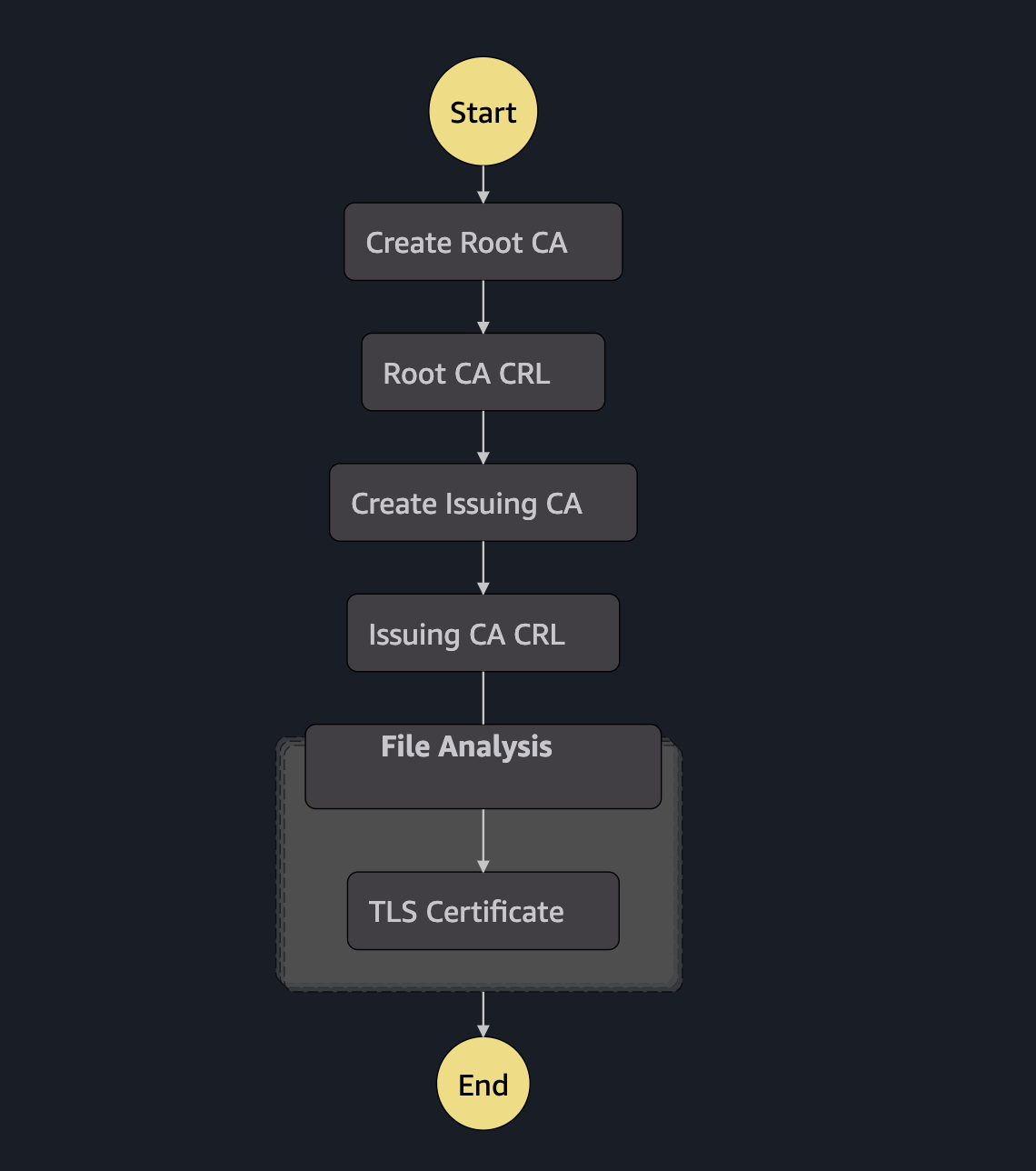
3. Flexible Cryptographic Options
Support for both ECDSA and RSA algorithms provides organizations the flexibility to choose the most appropriate cryptographic approach for their specific use cases, balancing performance, compatibility, and security requirements.
4. Advanced Management Capabilities
Automated Certificate Lifecycle Management
- Automated Certificate Revocation List (CRL) publication
- Optional public CRL Distribution Points
- Centralized logging and comprehensive auditing
Granular Access Control
By leveraging advanced management for user permissions with tools such as AWS IAM, organizations can implement extremely fine-grained access controls, ensuring that certificate issuance and management follow the principle of least privilege.
Modern Operational Model: GitOps and Automation
By implementing a GitOps operating model, Private Cloud-Native CA eliminates manual processes, introducing:
- Consistent, version-controlled infrastructure
- Predictable and repeatable certificate management
- Enhanced compliance and auditability
What’s next ?
While public CAs serve an important role in internet security, organizations with heightened security requirements should seriously consider operating their own Certificate Authority.
The benefits of complete control, enhanced security, and potential cost savings make it an attractive option for organizations that handle sensitive information.
The investment in infrastructure and expertise required to run a private CA is significant, but for organizations where security is paramount, it’s an investment that pays dividends in terms of control, security, and peace of mind.
Remember: in an age where data breaches make headlines daily, taking control of your certificate infrastructure isn’t just about security—it’s about taking responsibility for your organization’s digital trust.
Transform your security infrastructure with a Private Cloud-Native Certificate Infrastructure.