Deep dive into Kubernetes Security
Table of Contents
Kubernetes Security
This article covers fundamental concepts, security practices, and advanced security measures to protect Kubernetes clusters.
K8s architecture and components
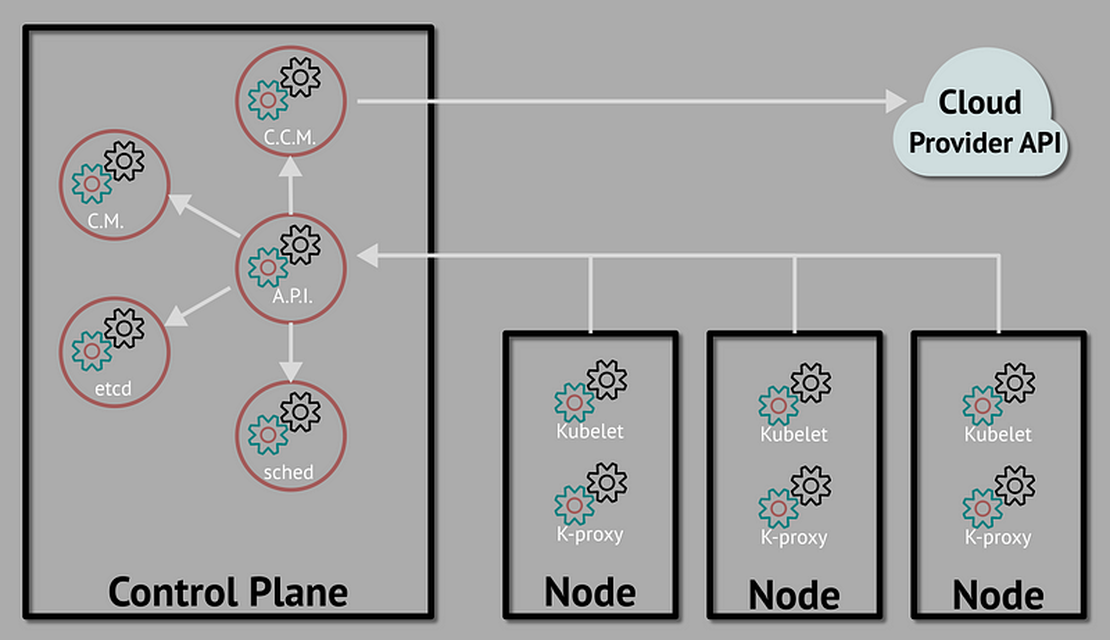
Kubernetes architecture is built around a cluster model, consisting of a control-plane node that manages the cluster and worker nodes that run the containerized applications.
Key components include the API server (for cluster management communication), etcd (a key-value store for cluster state), kubelet (runs on nodes to manage container operations), and kube-proxy (handles network communication).
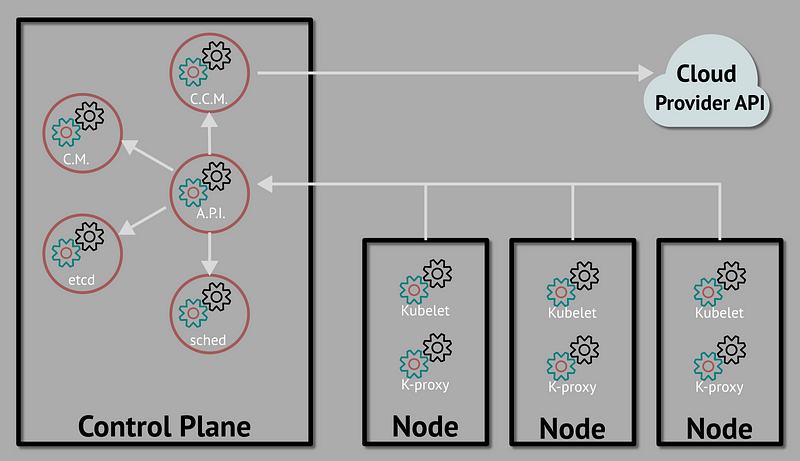
Basic Kubernetes operations involve deploying applications using Pods (the smallest deployable units), managing services that allow network access to Pods, and scaling or updating applications seamlessly with minimal downtime.
K8s security model
The Kubernetes security model is designed to provide strong isolation and security guarantees for applications running in a cluster, focusing on principles like least privilege, role-based access control (RBAC), and network policies to restrict access and communication.
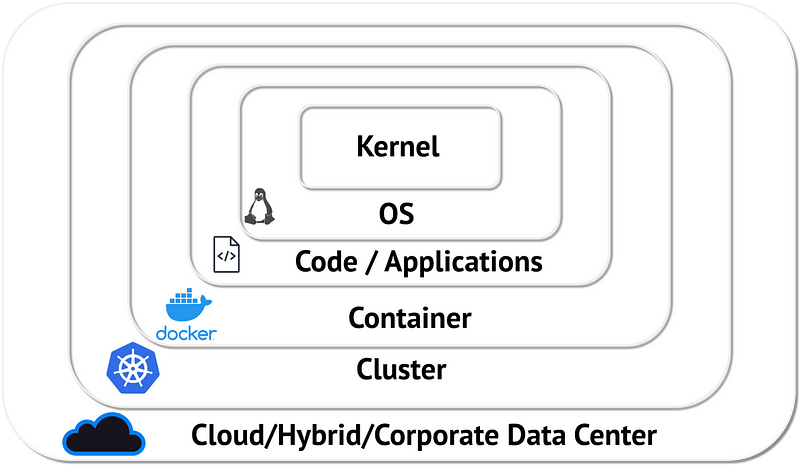
It operates at multiple layers, including cluster, network, and application levels, to secure cluster components, protect network traffic, and manage access to resources and workloads through authentication and authorization mechanisms.
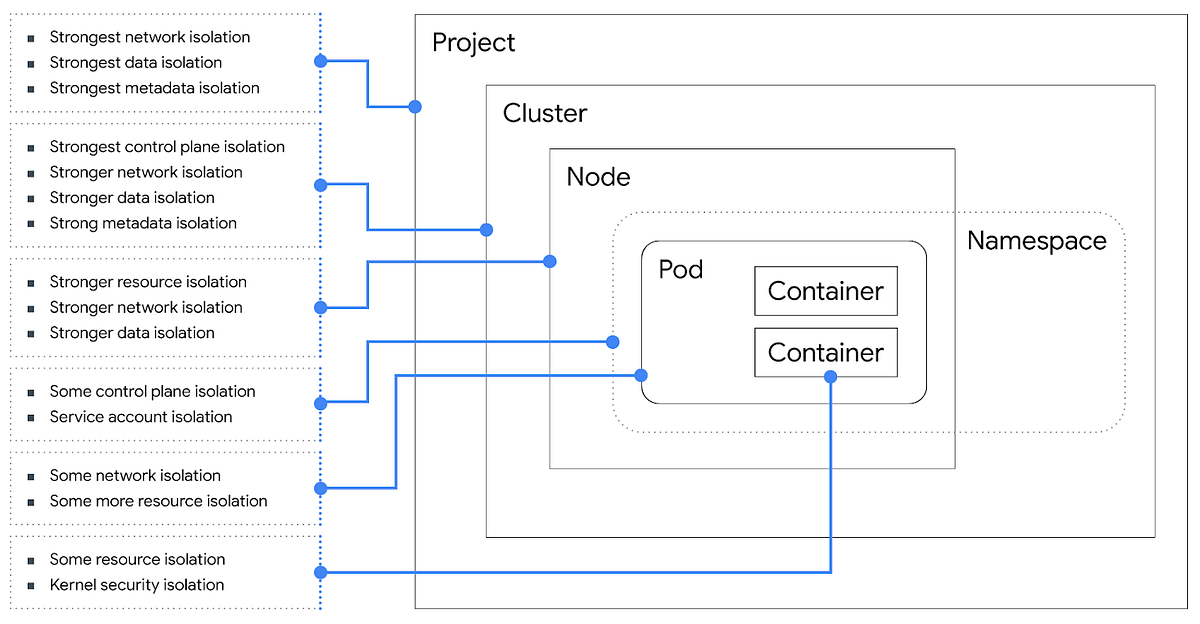
Securing the K8s cluster
Cluster setup and network security
Secure cluster setup practices in Kubernetes involve hardening node security, ensuring proper authentication and authorization mechanisms like RBAC are in place, and using encryption for data at rest and in transit to protect sensitive information.
Implementing network policies is crucial for defining how pods can communicate with each other and with other network endpoints, effectively limiting the blast radius of potential attacks by isolating pods and preventing unauthorized access.
This setup enhances the overall security posture of the Kubernetes cluster by minimizing attack surfaces and enforcing the principle of least privilege at the network level.
Authentication and authorization
Kubernetes supports multiple authentication methods, including static tokens, certificates, basic authentication, and external identity providers through plugins, allowing for flexible integration with existing authentication systems.
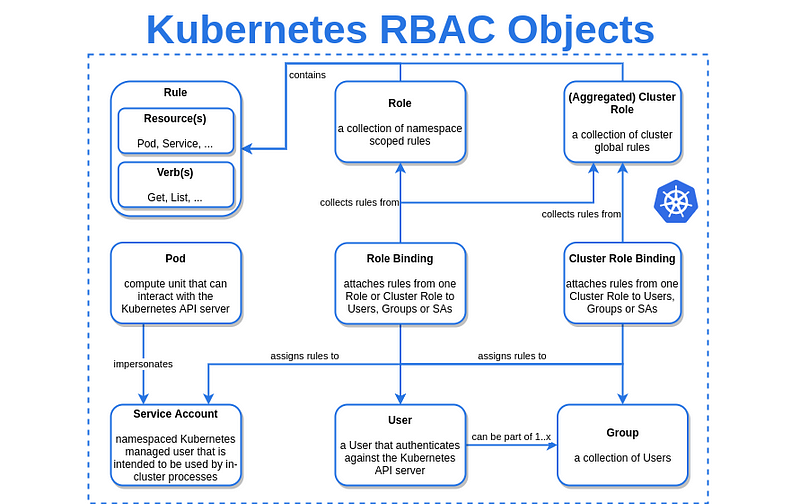
Once authenticated, Role-Based Access Control (RBAC) is used to determine what actions the authenticated entities are allowed to perform.
RBAC in Kubernetes works by associating roles, which define permissions to resources, with subjects (users, groups, or service accounts) through role bindings or cluster role bindings for cluster-wide permissions, allowing fine-grained access control based on the principle of least privilege.
API Server Security
Securing communications with the Kubernetes API server involves enabling TLS encryption for all API traffic, ensuring that both the data in transit is protected and that clients verify the server’s identity via certificates.
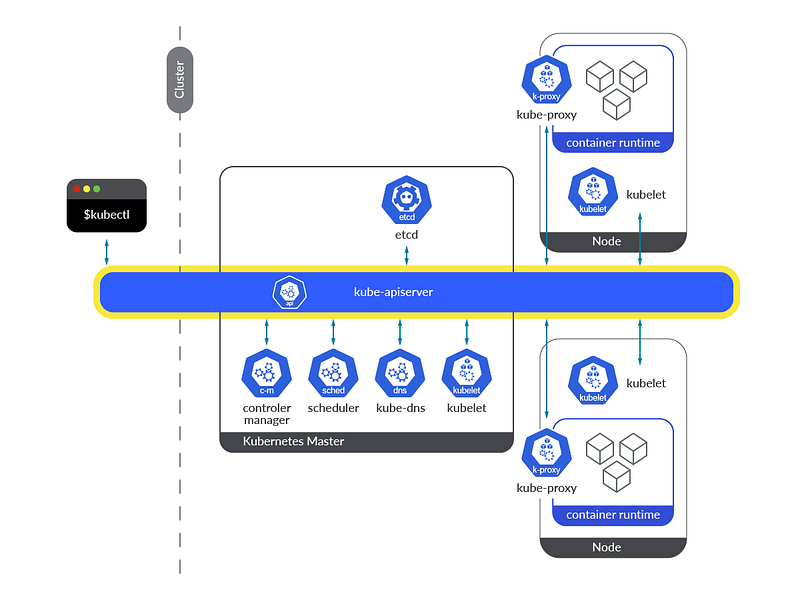
Additionally, using authentication mechanisms and network policies to control access to the API server helps prevent unauthorized access and potential data breaches.
Auditing API access involves tracking and logging every call to the API server, including who made the call, what was requested, and the response, which is crucial for security analysis, identifying potential unauthorized access, and ensuring compliance with security policies.
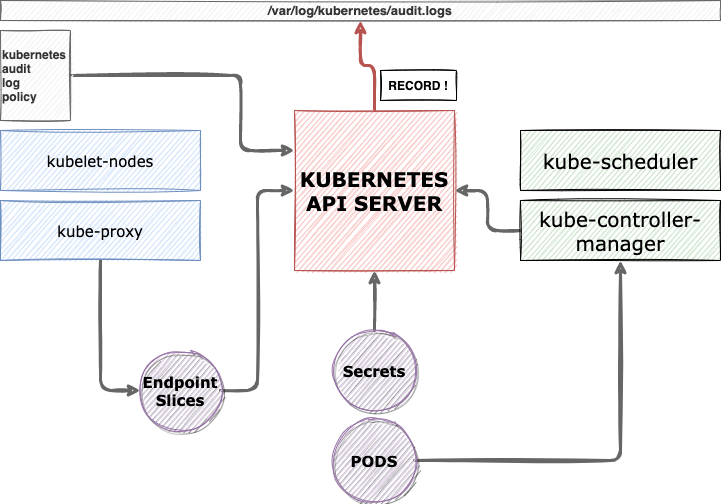
It provides a traceable record that can be analyzed for suspicious activities, contributing to the overall security posture of the cluster.
Workload Security
Kubernetes workloads are often the primary target of attacks within a cluster. They run the applications and processes that handle sensitive data, business logic, and user transactions.
A breach at the workload level can lead to unauthorized data access, data theft, service disruption, and a compromised cluster environment.
Pod Security Standards and Admission
Pod Security Standards in Kubernetes are a set of predefined rules that enhance the security of pod deployments by restricting their capabilities, such as preventing privileged access, limiting host filesystem access, and controlling the use of other sensitive features.
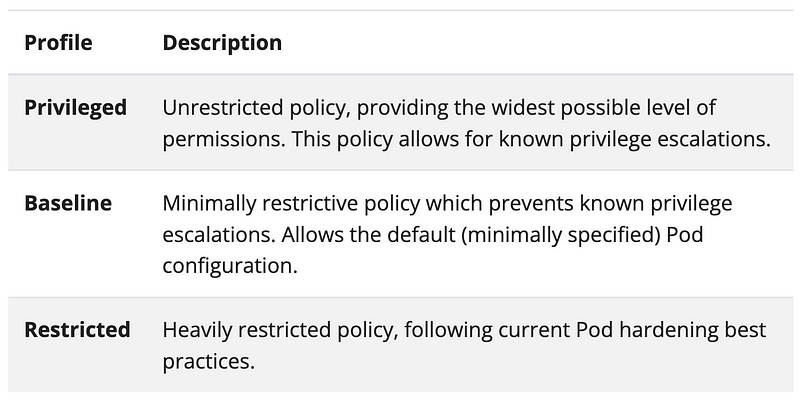
These standards are categorized into three levels: privileged, baseline, and restricted, providing a progressively tighter security posture.
The Pod Security Admission (formerly known as Pod Security Policies) plays a crucial role in Kubernetes security by enforcing these standards at the admission stage, ensuring that pods comply with the defined security policies before they are allowed to run in the cluster, thereby mitigating potential security risks from less secure configurations.
Container security
Securing container images is vital because they form the foundation of Kubernetes workloads; compromised images can introduce vulnerabilities into the environment, leading to potential breaches and unauthorized access.
In practice, securing container images involves using trusted base images, scanning images for vulnerabilities regularly, and implementing image signing to ensure integrity.
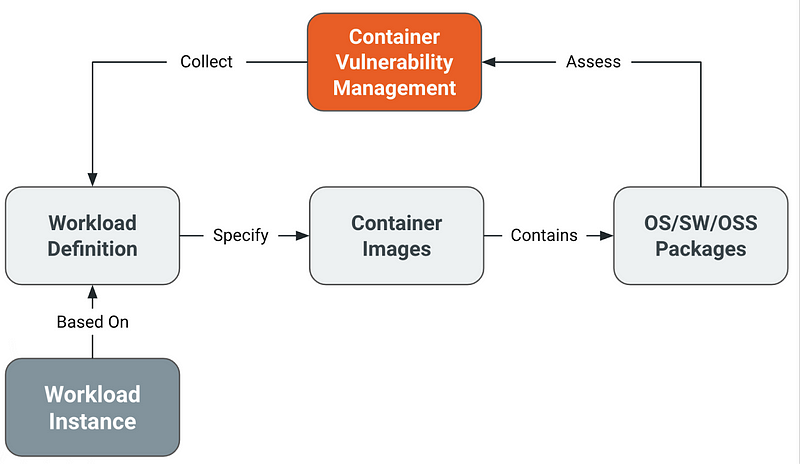
Managing container vulnerabilities requires a continuous approach, including automating the scanning of images in the CI/CD pipeline, promptly updating images with patches for known vulnerabilities, and employing tools for runtime security monitoring to detect and mitigate threats dynamically.
Protecting the secrets
Managing secrets in Kubernetes, such as passwords, tokens, and keys, is essential for maintaining the security and integrity of applications and access controls within the cluster.
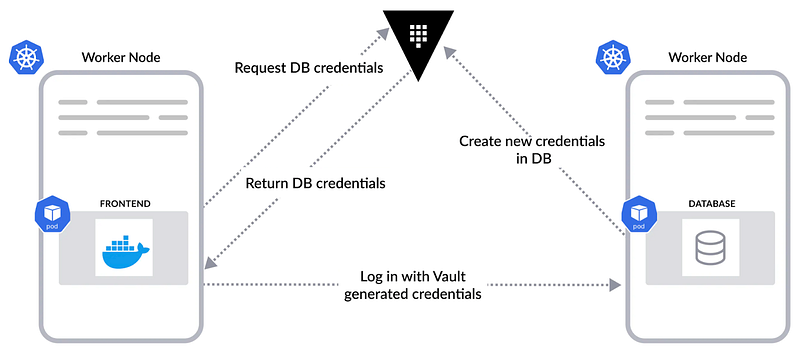
Secrets need to be handled carefully to prevent unauthorized access and exposure, especially when they are stored, or “at rest,” within the cluster’s etcd database.
Encrypting secrets at rest is a critical security measure that protects these sensitive values from being readable by unauthorized users or attackers who might gain access to the etcd datastore, thereby ensuring that sensitive information remains confidential and is only accessible to authorized components and users within the cluster.
# Run this as an administrator that can read and write all Secrets
kubectl get secrets - all-namespaces -o json | kubectl replace -f -
K8s Security Monitoring
Logging and monitoring
Collecting and analyzing logs across the cluster’s components, including nodes, pods, and containers, is crucial for identifying security incidents, diagnosing system errors, and understanding application behavior.
This practice enables timely detection of anomalies, potential vulnerabilities, and active threats, facilitating quick response and remediation actions to safeguard the cluster’s security posture and ensure the continuous, secure operation of services.

Tools like Prometheus for monitoring and Grafana for visualization offer powerful capabilities to observe the health and performance of Kubernetes clusters, providing insights through metrics and alerts.
For log collection and analysis, Elasticsearch, Fluentd, and Kibana (EFK stack) or Loki for more efficient log processing, enable centralized logging, facilitating deep analysis and real-time monitoring of security events and operational issues across the cluster.
Anomaly detection
Setting up anomaly detection in Kubernetes is crucial for identifying unusual behaviors that could indicate security incidents, breaches, or vulnerabilities being exploited, allowing for rapid response before significant damage occurs.
By leveraging machine learning and rule-based algorithms, anomaly detection tools can sift through vast amounts of data to spot deviations from normal operational patterns.
To effectively respond to security incidents, organizations should implement incident response plans that include immediate isolation of affected components, thorough investigation to understand the breach’s extent, and remediation steps to secure the cluster against future attacks.
Integrating security tools with alerting mechanisms ensures that anomalies trigger timely notifications, enabling swift action to mitigate threats.
Network Security
Using Service Meches
Implementing service meshes like Istio in Kubernetes environments is important because they provide an additional layer of security, including strong identity-based authentication and authorization between services, and encryption of data in transit within the cluster.

These capabilities enable fine-grained control over traffic flow and access policies, significantly enhancing security by ensuring that only authorized services can communicate with each other, thereby reducing the potential attack surface within microservices architectures.
Managing TLS, Ingress and Egress
Configuring TLS (Transport Layer Security) for secure communication within a Kubernetes cluster ensures that data transmitted between services is encrypted, protecting it from eavesdropping, tampering, and forgery. This is crucial for maintaining the confidentiality and integrity of sensitive data as it moves within the cluster.
Managing ingress and egress efficiently, through policies that control the flow of traffic into and out of the cluster, helps to enforce security boundaries around the services, preventing unauthorized access and limiting the potential for malicious activities.

Together, these practices improve Kubernetes security by safeguarding data in transit and controlling access points to and from the cluster, minimizing vulnerabilities.
Advanced Security Practices
Security Contexts
Kubernetes Security Contexts define privilege and access control settings for pods and containers, specifying how the processes within them are run and interact with the underlying system and other resources.

Implementing security contexts involves configuring settings such as running processes as non-root users, enforcing read-only root file systems, and limiting network access and privilege escalation, which can be applied at the pod or container level to enhance the security posture of the workloads running in a Kubernetes cluster.
Admission Controllers
Kubernetes Admission Controllers are powerful plugins that act as gatekeepers, intercepting requests to the Kubernetes API server before object persistence or creation, to enforce governance and security policies.
Configuring and customizing Admission Controllers involves enabling specific controllers that align with security policies, such as validating admissions to reject objects that don’t comply with security standards, or mutating admissions to modify objects to ensure compliance.
This process enhances security by ensuring only secure and compliant resources are allowed to run, providing an automated mechanism to enforce organizational policies and best practices across the Kubernetes environment.
Compliance and best practices
Kubernetes Security Benchmark
The CIS Kubernetes Benchmark is a set of guidelines and best practices developed by the Center for Internet Security to secure Kubernetes environments, covering areas like configuration, network policies, and system logging.
Ensuring compliance with these benchmarks involves regularly auditing the Kubernetes cluster against the CIS guidelines, using automated tools to detect deviations and non-compliant configurations, and then applying necessary changes to meet the benchmark standards.

This process helps maintain a robust security posture by adhering to industry-recognized practices and minimizing vulnerabilities within their Kubernetes infrastructure.

Security Assessments and Patch management
Building on the importance of adhering to security benchmarks like the CIS Kubernetes Benchmark, conducting regular security assessments becomes an indispensable next step.

These assessments help uncover potential vulnerabilities and misconfigurations that could deviate from established security practices, thereby preempting possible exploitation.
Furthermore, integrating patch management into this regimen ensures that all components of the Kubernetes cluster — ranging from the core Kubernetes software to the containerized applications it hosts — are consistently updated.
This not only rectifies known security flaws but also fortifies the cluster’s defenses with the latest security features and improvements, reinforcing the cluster’s resilience against emerging threats.
Conclusion
In conclusion, securing a Kubernetes environment is multifaceted, involving the diligent application of best practices across cluster setup, workload protection, network policies, and access controls.
Emphasizing the importance of securing container images, managing secrets safely, and enforcing role-based access control (RBAC) cannot be overstated.
Regularly conducting security assessments, staying compliant with benchmarks like the CIS Kubernetes Benchmark, and keeping the cluster and its components updated are critical for maintaining a strong security posture.
Tools such as service meshes and TLS configurations play a vital role in enhancing communication security, while admission controllers ensure that only compliant resources are deployed.
Ultimately, the collective implementation of these strategies forms a robust defense against potential vulnerabilities and threats, safeguarding your Kubernetes environment and the valuable applications it hosts.
One last thing
Hope you enjoyed the article. If this story provided value and you wish to show a little support, you could:
- Clap a lot of times for this story 👏👏👏
- Highlight the parts more relevant to be remembered (it will be easier for you to find it later, and for me to write better articles)
- Follow me on Medium
- Read my latest articles https://medium.com/@araji
Here some few more resources:
ArgoCD deployment patterns: “App of Apps” Vs. ApplicationSets
_Kubernetes has emerged as the de-facto platform for modern containerized applications._araji.medium.com
Kubernetes Security : Monitor Audit logs with Grafana
_Monitoring Kubernetes audit logs plays an important role in strengthening the overall security posture of the…_araji.medium.com
[Kubernetes Policy-as-Code : Kyverno Vs. OPA