“Essential Security for Event-Driven Architectures
- Molntek
- July 19, 2024
Table of Contents
Event-driven systems have become integral to large enterprise architectures, often serving as their core. This article explores the crucial importance of securing these systems and outlines the key security considerations necessary to prevent dangerous breaches.
These security controls can apply to any event-based streaming tool, this article uses Apache Kafka for its widespread use within the enterprise ecosystem.
Outline
- What are Event-Driven Systems
- Why Does Security Matters ?
- Top 10 security considerations
Event-Driven systems
Event-based systems have become a cornerstone of modern software architectures due to their ability to handle complex, real-time data processing, scalability, and flexibility.
These systems enable software components to react to events asynchronously, facilitating more responsive and resilient applications.
The rise of microservices architecture has further amplified the importance of event-based systems where independent microservices communicate through events, enabling more scalable and maintainable systems.
Securing event-based systems is paramount due to their critical role in modern software architectures and the sensitive nature of the data they handle. These systems are increasingly targeted by cyber threats aiming to exploit vulnerabilities for malicious purposes.
Security implications
1. Data Integrity and Confidentiality
Event-based systems often process and transmit sensitive data. For instance, in the financial trading platforms example above, if these systems are compromised, it could lead to data breaches, financial losses, and legal ramifications.
Securing the system ensures that data remains accurate and confidential, protecting both users and the organization from potential harm.
“By default, there is no encryption or authentication, nor are ACLs configured. Any client can communicate to a Kafka brokers using the PLAINTEXT port. It is critical that access using this port is restricted to trusted clients only.” — Official Confluent documentation
2. Operational Continuity and Availability
The availability of event-based systems is crucial for maintaining operational continuity. In e-commerce platforms, real-time inventory management and order processing rely on the uninterrupted flow of events.
Any security breach could disrupt these operations, leading to lost sales, damaged reputation, and decreased customer trust.
Robust security measures help prevent such disruptions by safeguarding against attacks that could cause system outages or slowdowns.
3. Compliance and Regulatory Requirements
Many industries are subject to strict regulatory requirements regarding data protection and security. For example, the healthcare sector must comply with regulations like HIPAA, while the financial sector adheres to standards such as PCI DSS.
Event-based systems in these industries must be secured to ensure compliance, avoiding hefty fines and legal consequences.
4. Mitigation of Advanced Cyber Threats
As cyber threats become more sophisticated, event-based systems are at risk of advanced persistent threats (APTs), ransomware, and other forms of cyber attacks. For example, a coordinated attack on a smart grid’s event-driven infrastructure could disrupt energy distribution, causing widespread blackouts and economic disruption.
Implementing strong security measures helps mitigate these risks by protecting against unauthorized access and ensuring system integrity.
Top 10 security considerations
To illustrate what security considerations translate on a real enterprise-level event-system, we are using Apache Kafka. Kafka provides a robust and scalable foundation for building modern, event-driven, and data-intensive applications and is used by 80% of Fortune 100 companies around the world.
Using Apache Kafka in an enterprise setting involves several security considerations to ensure data integrity, confidentiality, and availability. Here are the key security aspects to consider:
1. Authentication and Authorization
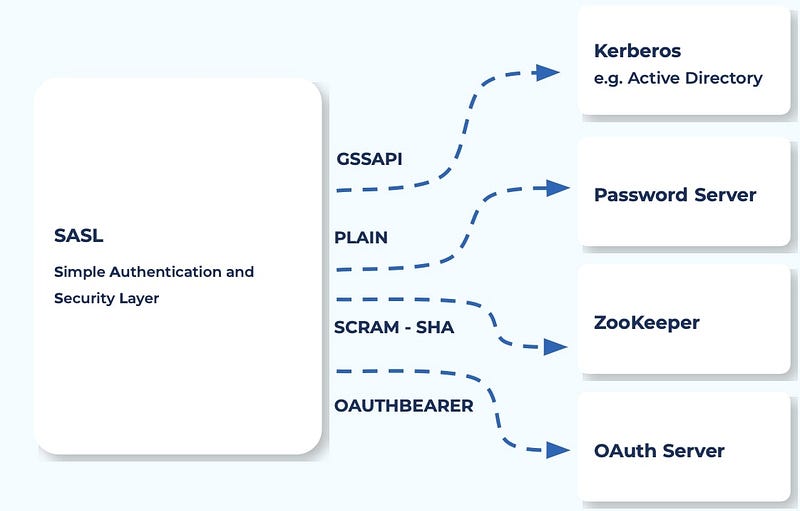
- Authentication: Implement robust authentication mechanisms to verify the identity of clients and brokers. Use SASL (Simple Authentication and Security Layer) with Kerberos, SCRAM, or OAuth for secure authentication.
- Authorization: Use Apache Kafka’s built-in access control lists (ACLs) to define permissions for topics, consumer groups, and other resources. Ensure that only authorized users and applications can perform actions on specific Kafka resources.
2. Encryption
- Encryption at Rest: Encrypt data stored on disk to protect it from unauthorized access. This can be achieved using disk encryption tools or Kafka’s own features.
- Encryption in Transit: Enable SSL/TLS to encrypt data as it travels between clients, brokers, and ZooKeeper nodes. This helps prevent man-in-the-middle attacks and ensures data privacy.
3. Network Security
- Segmentation: Use network segmentation to isolate Kafka brokers, ZooKeeper nodes, and clients. Limit access to the Kafka cluster to only trusted networks and clients.
- Firewall and Security Groups: Configure firewalls and security groups to restrict inbound and outbound traffic to Kafka brokers and ZooKeeper nodes based on IP addresses and port numbers.
4. Monitoring and Auditing
- Logging: Enable and monitor Kafka logs for unusual activities or security incidents. This includes access logs, error logs, and audit logs.
- Monitoring Tools: Use monitoring tools such as Prometheus, Grafana, or Kafka’s own JMX metrics to keep track of the cluster’s health and detect potential security breaches.
- Auditing: Implement auditing mechanisms to track access and changes to the Kafka cluster. This can help in forensic analysis and compliance with regulations.
5. ZooKeeper Security
- Authentication and ACLs: Enable authentication and configure ACLs for ZooKeeper to control access to its data.
- Encryption: Use TLS to encrypt communication between Kafka brokers and ZooKeeper.
“With ZooKeeper being deprecated in favor of the KRaft (Kafka Raft) mode, it’s essential to adapt security practices to ensure the continued protection of your Kafka deployment.”
6. Cluster Configuration
- Secure Configuration: Regularly review and update Kafka’s configuration files to ensure they follow security best practices. Avoid hardcoding sensitive information and use environment variables or secure vaults.
- Configuration Management: Use configuration management tools to enforce security settings consistently across all nodes in the Kafka cluster.
7. Security Practices and Policies
- Principle of Least Privilege: Grant the minimum necessary permissions to users and applications.
- Regular Security Reviews: Conduct regular security reviews and audits of the Kafka cluster and its configurations.
- Incident Response: Develop and maintain an incident response plan specific to your Kafka deployment.
8. Backup and Disaster Recovery
- Regular Backups: Ensure that backups of critical Kafka data and configurations are performed regularly and stored securely.
- Disaster Recovery Plan: Develop and test a disaster recovery plan to ensure business continuity in case of a security incident or failure.
9. Data Governance and Compliance
- Data Masking and Anonymization: Implement data masking or anonymization techniques to protect sensitive data being processed by Kafka.
- Compliance: Ensure that your Kafka deployment complies with relevant data protection regulations such as GDPR, HIPAA, or CCPA.
10. User Education and Training
- Security Awareness: Train users and administrators on security best practices and the specific security features of Apache Kafka.
- Role-based Training: Provide role-specific training for developers, operators, and security personnel involved with Kafka.
By addressing these security considerations, you can enhance the security posture of your Apache Kafka deployment and protect your enterprise data effectively.
Conclusion
In summary, the importance of event-based systems in modern software architectures lies in their ability to provide real-time processing, enhance scalability, and improve system responsiveness and flexibility.
In this article I presented how securing event-based systems is essential to protect sensitive data, ensure operational continuity, comply with regulatory requirements, mitigate advanced cyber threats and enhance business competitiveness.
As these systems become more integral to modern software architectures, investing in their security becomes more than just a necessity.
Further Reading
To dig deeper, I list below some interesting references that might help you build a better grasp on how to apply the aforementioned controls to secure your Apache Kafka (or any similar event-based and streaming service):