Kubernetes Policy-as-Code : Kyverno Vs. OPA
Table of Contents
Kubernetes Security
Kubernetes security with policy-as-code refers to automating and enforcing security policies directly within the deployment pipeline.
Two notable tools in this space are Kyverno and Open Policy Agent (OPA).

This article highlights the motivation behind such tools, the key differences between Kyverno and OPA and why you should consider using them as part of your Kubernetes infrastructure.
Motivation
Including tools like a Policy-as-Code tool in a Kubernetes cluster significantly enhances its security posture.
Such a tool should automate the enforcement of security policies, ensuring that all deployed resources comply with organizational standards and security best practices.
This can minimizes human errors, reduces the risk of security breaches, and ensures consistent policy application across all cluster resources.
Moreover, it supports a shift-left security approach, identifying and mitigating vulnerabilities early in the development cycle.
The benefits include improved security, compliance, and operational efficiency within Kubernetes environments.
Kyverno Vs. OPA
Kyverno is a Kubernetes-native policy engine that allows you to manage policies as Kubernetes objects, without writing complex rego queries.
It integrates seamlessly with Kubernetes, offering a high level of abstraction suitable for Kubernetes resources.
Open Policy Agent (OPA), on the other hand, is a more generic, open-source policy engine that can be used across various technologies, including Kubernetes.
It uses a high-level declarative language called Rego for writing policies.
Both tools enable dynamic policy enforcement across your Kubernetes clusters, but they differ in their approach and flexibility:
- Kyverno is easier for Kubernetes-specific use cases due to its native integration and simpler policy language.
- OPA offers greater versatility and is better suited for organizations looking for a unified policy framework across different technologies, not just Kubernetes.
Example Policies:
- Kyverno Example: Enforce labels on Pods.
apiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: require-labels
spec:
rules:
- name: check-for-labels
match:
resources:
kinds:
- Pod
validate:
message: “Missing mandatory label ‘app’”
pattern:
metadata:
labels:
app: “?*”
- OPA Example: Ensure all images come from a trusted registry.
package kubernetes.admission
deny[msg] {
input.request.kind.kind == “Pod”
image := input.request.object.spec.containers[_].image
not startswith(image, “trusted-registry.io/”)
msg := sprintf(“untrusted image registry for image: %v”, [image])
}
How the Policy Engine Works:
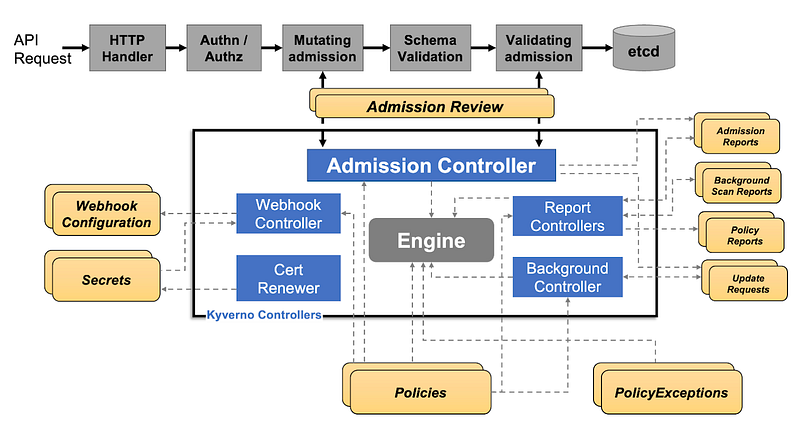
- Kyverno intercepts API requests to the Kubernetes API server using a webhook and applies the policies defined in its CRDs (Custom Resource Definitions) to these requests.
If a request violates a policy, Kyverno blocks the request and returns an error message.
- OPA uses a similar approach with its admission controller webhook.
When Kubernetes API requests are made, OPA evaluates these requests against the policies defined in Rego.
If a request violates a policy, OPA denies the request and returns a message explaining the violation.
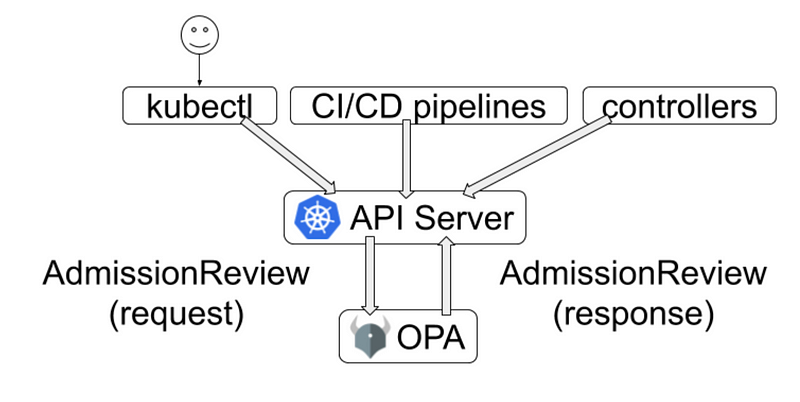
Both engines operate on the principle of intercepting requests to the Kubernetes API server and evaluating them against predefined policies, ensuring that only compliant resources are deployed.
This method strengthens the security posture of Kubernetes environments by ensuring consistent policy enforcement across all deployments.
Why do you need to get one ?
To explore how policy-as-code tools can automate and enhance the security and operational management of Kubernetes clusters, let’s explore some use cases:
1. Enforcing Security Best Practices: Automatically enforcing security standards, such as requiring all containers to run as non-root users, to minimize potential vulnerabilities.
2. Compliance Auditing: Ensuring clusters are compliant with regulations like GDPR or HIPAA by enforcing policies that control data access and processing.
3. Resource Management: Limiting resource consumption on a per-namespace or per-pod basis to prevent any single application from monopolizing cluster resources.
4. Multi-Tenancy Support: Isolating workloads from different teams or projects within the same cluster, ensuring data privacy and resource allocation fairness.
5. Image Assurance: Restricting container images to those from approved registries or with specific tags to prevent the use of outdated or vulnerable software.

6. Secret Management: Enforcing policies to automatically encrypt secrets stored in etcd, enhancing data protection.
7. Network Policies: Defining fine-grained network policies to control traffic flow between pods, thereby enhancing network security.
8. Pod Security Policies: Replacing deprecated PodSecurityPolicies with custom policies that restrict the use of privileged containers and enforce security contexts.
9. CI/CD Integration: Integrating policy checks into CI/CD pipelines to ensure only compliant code and configurations are deployed, reducing the risk of introducing vulnerabilities.
10. Automated Incident Response: Triggering automated responses to policy violations, such as alerting, blocking deployments, or rolling back to a safe state.
The takeaway
Automating policy enforcement with Kyverno or OPA streamlines operations and frees up valuable resources. Security teams can focus on defining and updating policies rather than manually auditing and enforcing them.
This operational efficiency can lead to faster deployment times, reduced operational costs, and a more focused allocation of security resources.
In conclusion, incorporating Kyverno or OPA into your Kubernetes infrastructure is not just about enhancing security; it’s about building a more robust, compliant, and efficient deployment pipeline that scales with your needs.
Whether you prioritize ease of use, specific Kubernetes integrations, or a more general policy framework, these tools offer significant advantages for managing modern cloud-native environments.
Before you go!
If you liked this article and you want to encourage me publishing more:
- Throw some Medium love 💕(claps, comments and highlights), your support means a lot to me.👏