Kubernetes: Security Blind Spot You Can’t Afford to Ignore
- Molntek
- Application , Cloud computing , Dev ops , Kubernetes , Security
- March 23, 2024
Table of Contents
Cloud Security
This article delves into essential and advanced security practices for Kubernetes clusters, from securing cluster architecture to enforcing access controls. It explains Kubernetes’ multi-layered security model, covering authentication, authorization, network policies, and role-based access control (RBAC). Key strategies for protecting workloads, managing container vulnerabilities, and securing sensitive secrets are discussed in-depth. It also highlights the importance of continuous security monitoring and anomaly detection to maintain a resilient and secure Kubernetes environment.
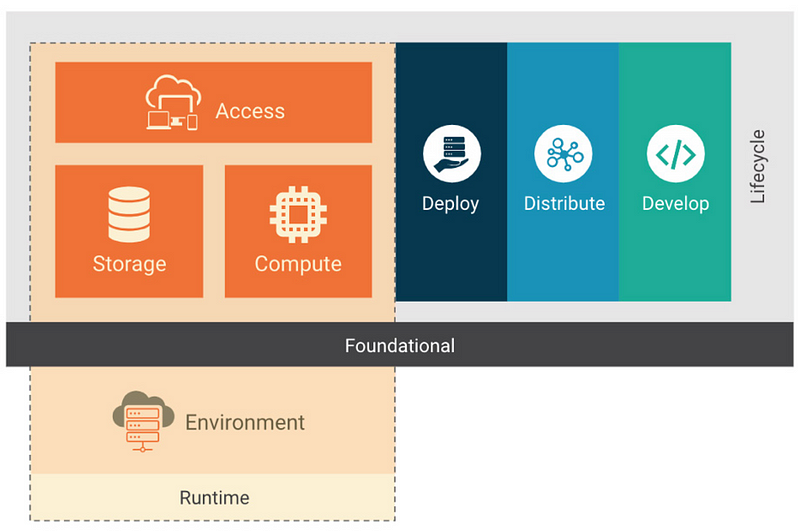
Lifecycle: Develop, Distribute, Deploy
Develop
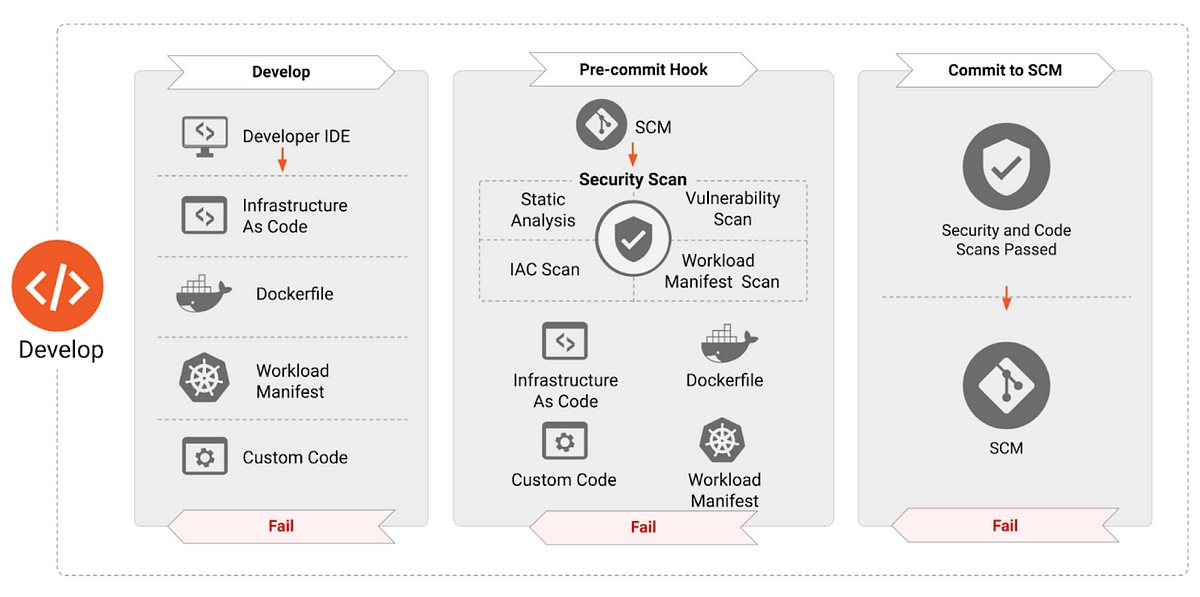
The “Develop” phase sets the stage for your application’s security posture. Artifacts like Infrastructure as Code, application manifests, and container definitions created here can contain vulnerabilities readily exploitable in the runtime environment.
Security hardening during the development phase is essential for a secure application deployment. Security requirements should be integrated into the software development process from the early phases, receiving the same priority as other design considerations.
Security requirements are generally derived from business risk assessments and potential industry compliance mandates, and may be the result of a threat modeling exercise.
Addressing these requirements early in the development cycle prevents costly rework later, ensuring DevOps efficiency and reducing overall costs.
DevOps teams must leverage tools designed to identify security misconfigurations and vulnerabilities before application deployment.
This means scanning Infrastructure as Code templates and application manifests within the IDE or during pull requests, providing actionable security insights early in the pipeline.
Security tools must integrate seamlessly with existing DevOps workflows.
Teams should implement dedicated development, testing, and production environments. This isolation allows developers to securely build, test, and deploy systems, applications, container base images, and conduct non-functional tests.
Distribute
The “Distribute” phase builds artifacts like container and VM images, guided by image definitions. Modern CI/CD pipelines prioritize testing in this phase to uncover software bugs.
However, reliance on open-source packages creates a risk, as they may contain hidden vulnerabilities or malware within the images. Therefore, security must be a core focus in this phase.
Implement robust image scanning to detect threats and verify image integrity to ensure they haven’t been compromised or tampered with.
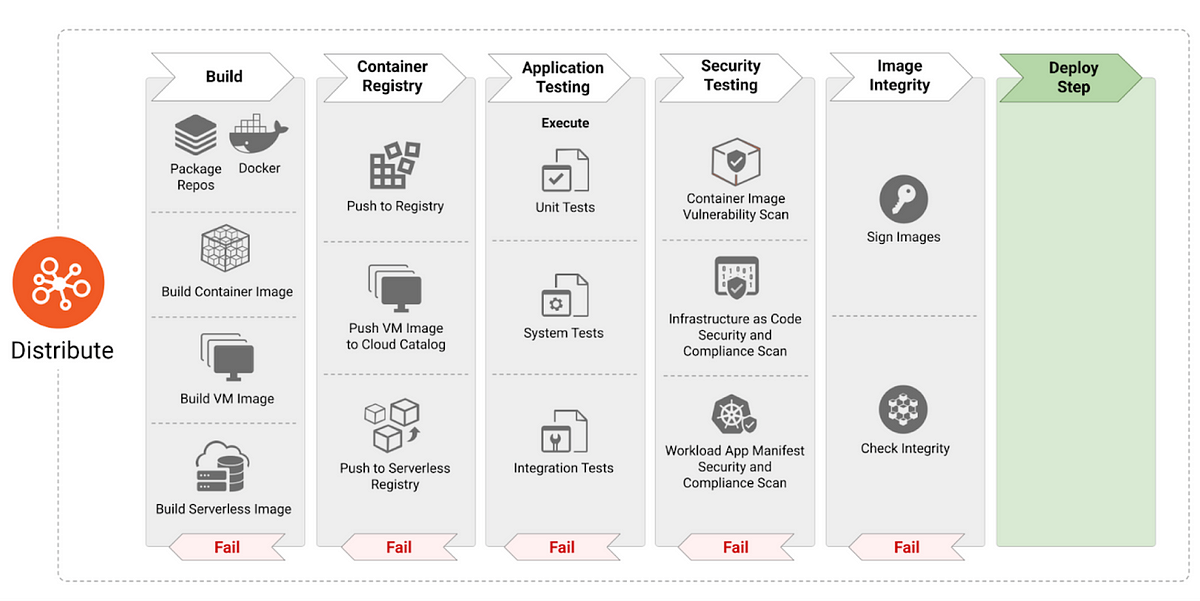
In addition to scanning, container images must include security hardening to mitigate any risks at the runtime phase by implementing controls such as:
- Restrict execution: Limit container processes to a specific, non-privileged user.
- Control resources: Enforce limits on resources (CPU, memory, etc.) available to the container.
- Impose kernel restrictions: Utilize kernel-level features to constrain what processes a container can execute.
Deploy
The “Deploy” phase mandates a series of ‘pre-flight’ checks to ensure applications meet organizational security and compliance policies before reaching the runtime environment.
Organizations must verify the following before deploying a container image:
- Image Integrity: Confirm image signature and that it hasn’t been tampered with.
- Image Runtime Policies: Check for malware or critical vulnerabilities.
- Container Runtime Policies: Ensure the container lacks excessive privileges.
- Host Compliance: Verify host-level vulnerability and compliance controls.
- Application and Network Security: Enforce workload, application, and network security policies.
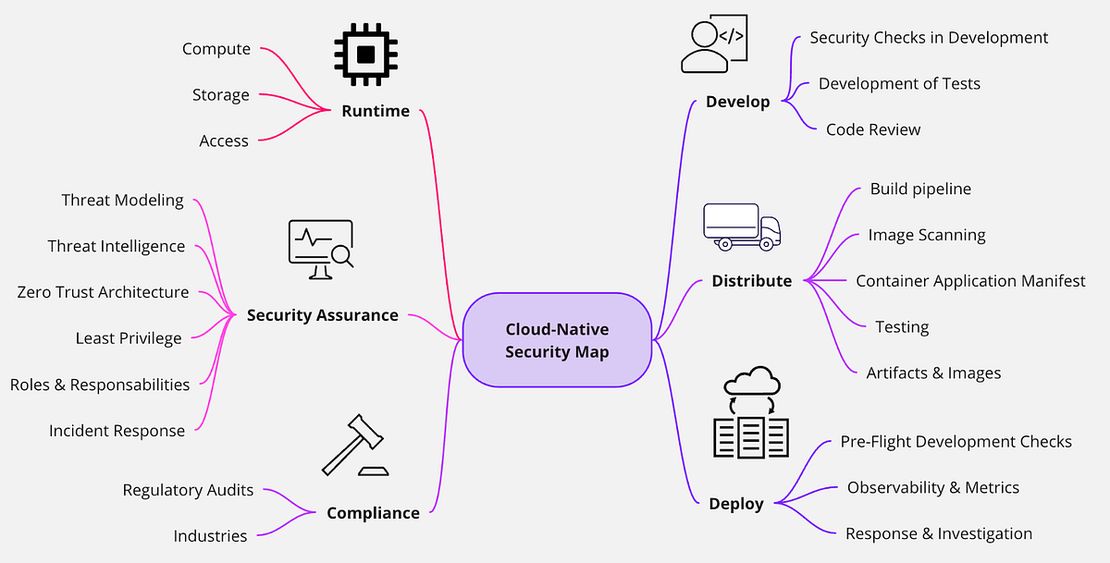
Runtime
Runtime security builds upon the foundation established in prior development phases (develop, distribute, deploy).
The Runtime phase is crucial and focuses on three key areas: compute, access, and storage.
Key runtime security aspects to take into account include:
Compute
- Container OS: Use a read-only, container-specific OS to minimize attack surface and provide resource isolation. Avoid sharing kernels between workloads with differing data sensitivity.
- Orchestrator Security: Protect the orchestrator’s API, key-value store, dashboard, and control plane traffic. Implement best practices and hardening to mitigate threats.
- Audit Logs: Automate analysis and correlation of audit logs to detect system compromise and abuse.
- Workload Monitoring: Monitor deployed workloads to ensure their operational state aligns with expectations. Detect unexpected or malicious behavior through system call and network traffic analysis.
Access
- Robust IAM: Implement service identity at minimum, with additional user/device identity for on-premises or hybrid clouds. Utilize identity federation in multi-cloud environments.
- Mutual Authentication: Explicitly authorize workload communication with mutual authentication. Use frequent, short-lived keys.
- Separate Decision and Enforcement: Ensure clear separation between authentication/authorization decision points and their enforcement across the environment.
- Attribute and Role-Based Access Control (ABAC & RBAC): Employ both for granular authorization and defense in depth. Ideally, leverage identity documents/tokens throughout the system to enable contextual authorization.
Storage
- Know Your Topology: Understanding centralized, distributed, or hyperconverged storage models informs the selection of specific security mechanisms to protect data in transit and at rest.
- Encryption: Implement data encryption for both data in transit and at rest to ensure confidentiality. Often integrated with a key management system.
- Volume Access Control: Define trust boundaries for namespaces to restrict volume access. Prevent cross-namespace volume mounting by privileged containers.
Core Elements of Cloud-Native Security
Modern cloud-native architectures drive innovation and value, but also demand a tailored security approach.
Start by conducting a thorough risk assessment, considering all aspects, from benefits to compliance, to inform your security and resilience strategies.
Key Actions:
- Visibility: Know your assets. Maintain a detailed inventory to pinpoint potential weaknesses.
- Compliance: Enforce relevant regulations (e.g., GDPR, HIPAA) through consistent security settings.
- Network Security: Analyze traffic patterns for privacy protection and threat detection.
- Identity and Access Management (IAM): Strictly control who (or what) can access your cloud resources.
- Data Protection: Encrypt data at rest, and monitor for breaches or malware.
- Vulnerability Scans: Regularly scan code, containers, and the runtime environment.
- Workload Security: Protect each component of your application, adapting as they change.
- Automation: Reduce the burden on teams by automating fixes for simple issues, and escalating complex ones.
Effective Strategies
Cloud-native security demands a proactive strategy due to the rapid evolution of both container technology and related threats. However, the following strategies are proven to be effective in this ever-changing landscape:
- Shared Responsibility: Clearly understand your responsibilities for securing your applications and data within your cloud provider’s infrastructure.
- Layered Security: Implement multiple safeguards across the entire stack, from user access to physical infrastructure. Consider firewalls, encryption, and other appropriate tools.
- Cloud-Agnostic Security: Choose tools compatible with multiple cloud platforms. This prevents vendor lock-in and simplifies security management.
Conclusion
While containers offer significant security advantages, realizing their full potential demands careful implementation. The visibility, modularity, and isolation they provide are key building blocks for a robust cloud-native security strategy.
By consistently applying security controls across development, testing, and production environments, as outlined earlier in this article, containers enhance your organization’s overall defense-in-depth strategy.
One last thing
Hope you enjoyed the article. If this story provided value and you wish to show a little support, you could:
- Clap for this story 👏👏👏
- Highlight the parts more relevant to be remembered (it will be easier for you to find it later, and for me to write better articles)
- Follow me on Medium
- Read my latest articles https://medium.com/@araji
Here some few more resources:
Monitoring Kubernetes Security Metrics with Prometheus and Kubescape
_A step-by-step guide to continuous Kubernetes security monitoring_araji.medium.com
Kubernetes Security : Monitor Audit logs with Grafana
_Monitoring Kubernetes audit logs plays an important role in strengthening the overall security posture of the…_araji.medium.com
Proactive Kubernetes Security: Unlocking Threat Detection with Kubescape, Prometheus, and Grafana
_A comprehensive guide to continuous security monitoring and visualization_araji.medium.com
I hope this deep dive into Cloud-Native security was insightful! 🚀 Ready to take your skills to the next level? Let’s connect and continue the conversation:
- Follow Me: Twitter:https://twitter.com/aminerj for updates, discussions, and more security best practices. 💡
- Questions or Feedback: Share your thoughts on the article or hit me up if you have any specific Kubernetes security challenges. 💬