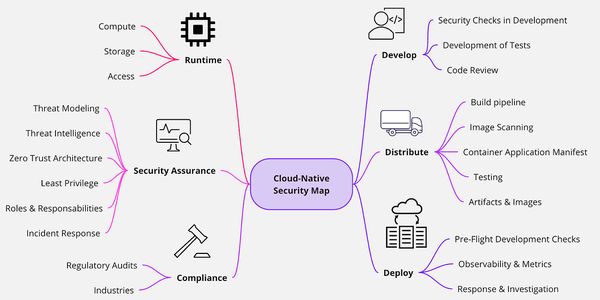
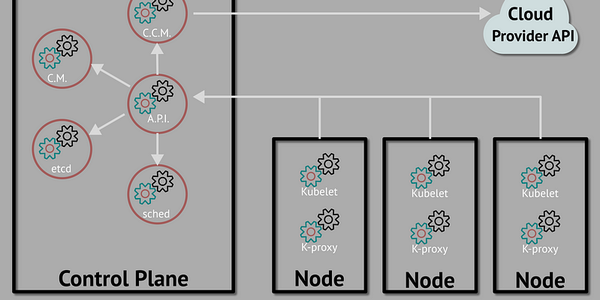
Cloud Security: Tools & Techniques for Server Hardening
Table of Contents
Cloud Security
Weather you opted for a Cloud service provider to move your IT resources to the Cloud or not, security is still your burden to deal with.
This article explains how to improve the security of your servers and demonstrate how hardening them can reduce the risks, using openly available state-of-the-art tools.

Security is “still” your responsibility, even in the Cloud
Using cloud services doesn’t mean you can outsource all of your security needs. Throughout the lifecycle of data in your company’s possession, security remains your responsibility.
You need to review your cloud contracts carefully to spell out your expectations and clearly establish who is primarily in charge of what.
If it’s your data, it’s ultimately your responsibility.
The rest of this article explains how to ensure that your servers (deployed virtual machines in the Cloud) are secure against most of the cyber threats. This process in the IT security jargon is referred to as hardening.
What is Server hardening
The National Institute of Standards and Technology (NIST) defines “hardening” as :
“A process used to patch vulnerabilities or turn off non-essential services.”
With hardening, your business can eliminate cybercrime attack vectors and unnecessary server processes.
For example, your company can harden access to certain system applications, ports, or user accounts. This removes potential vectors a cybercriminal can use to attack your company.
NIST’s Special Publication 800–123 offers standards and guidelines for hardening servers, such as:
- Create a security plan
- Patch and update your OS
- Remove or deactivate unnecessary applications, services, or network protocols
- Configure OS user authentication
- Utilize authentication and encryption technologies
The CIS Benchmarks also provide server configuration guidelines that are commonly used by businesses, educational institutions, and government agencies.
So, server hardening helps you guard against ransomware, malware, and other cyberthreats. You can follow this process to protect all points of entry against cyberattacks, address cybersecurity weaknesses, and optimise your security posture.
Why this is important ?
Not convinced yet ? Here is a simple glimpse of how it works when it comes to attacking resources connected to the Internet these days:
External attackers are continuously scanning the Internet to identify and target possibly unprotected connected machines. Attackers can take advantage of new assets that are installed, yet not securely configured and patched.
And this is if you are not targeted by the cyberattack.
According to some respected IT security sources (Google Project Zero, Palo Alto Unit42) , it takes less than five minutes sometimes for vulnerabilities to be exploited.
So, how to avoid that ?
There are several active measures to take to prevent such risks, one of them is hardening your servers. Here is the main two reasons why we choose to focus on this particular one:
- There are freely available tools that could help mitigate 99% of the risks
- This could be automated and aggregated as part of an overall continuous risk mitigation strategy
Let’s demonstrate how it works
- First, let’s deploy our server on the Cloud:
- Deploy a VM on your preferred Cloud provider (or locally). Here we are deploying a VM on Azure Cloud
- Make sure that you can connect (ssh) to your VM
2. Get the Free CIS Assessment Tool and run it
Return to your local browser and navigate to the CIS homepage, https://cisecurity.org. Scroll down to the bottom of the page locate the CIS-CAT Lite under the Tools section.
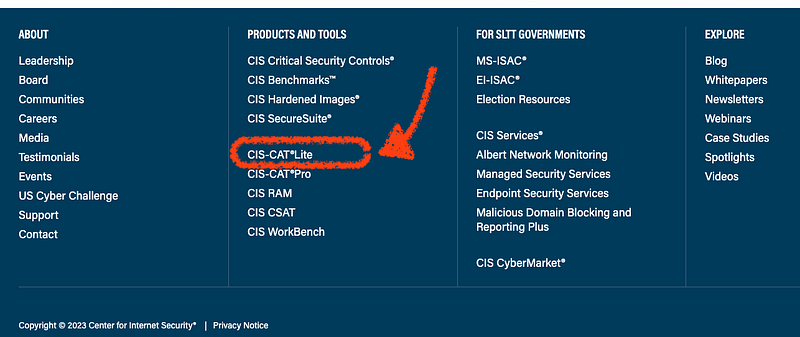
- Select the CIS-CAT Lite automated assessment tool. Note that under the Compare Key Features section the CIS Benchmarks supported only allows a select number of tools. The pro version for those with memberships has all available tools.
- We will test our Ubuntu server, both to ensure we are secure as well as to see a sample of what the assessment does and eventually returns. Fill out the form on the right and submit. This will cause an email to be sent to you with a link to download the tool.
- Inside the email you will eventually receive you will find the option to download the tool. While you may want to download the zip file locally to your machine, let us also download it to our VM. Instead of clicking on the green button, hover with the mouse over and copy the link. Then log into your exercise node and use the wget command to retrieve the file.
$ wget _<https://learn.cisecurity.org/e/ the very long link-...>_$ mv _<downloaded file name>_ CIS-Cat.zip$ sudo apt-get update ; sudo apt install unzip
Note that the assessment tool requires JAVA. Install the software then set the JAVA_PATH variable.
~/Assessor$ sudo apt-get install openjdk-11-jdk -y~/Assessor$ export JAVA_PATH=/usr/lib/jvm/java-11-openjdk-amd64/bin/- Run the tool
~/Assessor$ sudo bash Assessor-CLI.sh -i
When the Select Content prompt appears enter the number 6, to assess Ubuntu.
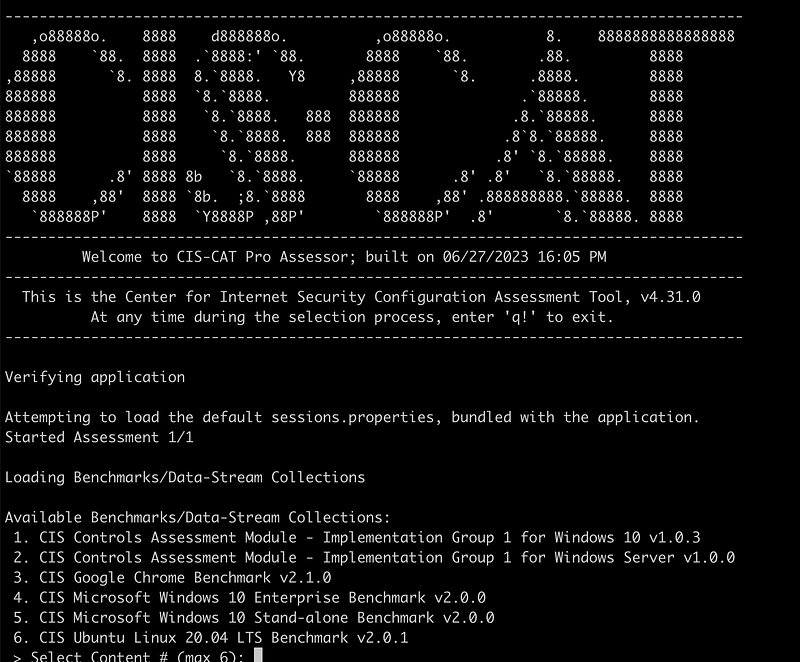
- You should then see options about what level of testing you want to do. Chose option1.
- There will be a lot of output following. Take a moment to scan through the hundreds of tests. Some will pass, some will fail. At the end of the output you should see total assessment time and a location for the HTML report.
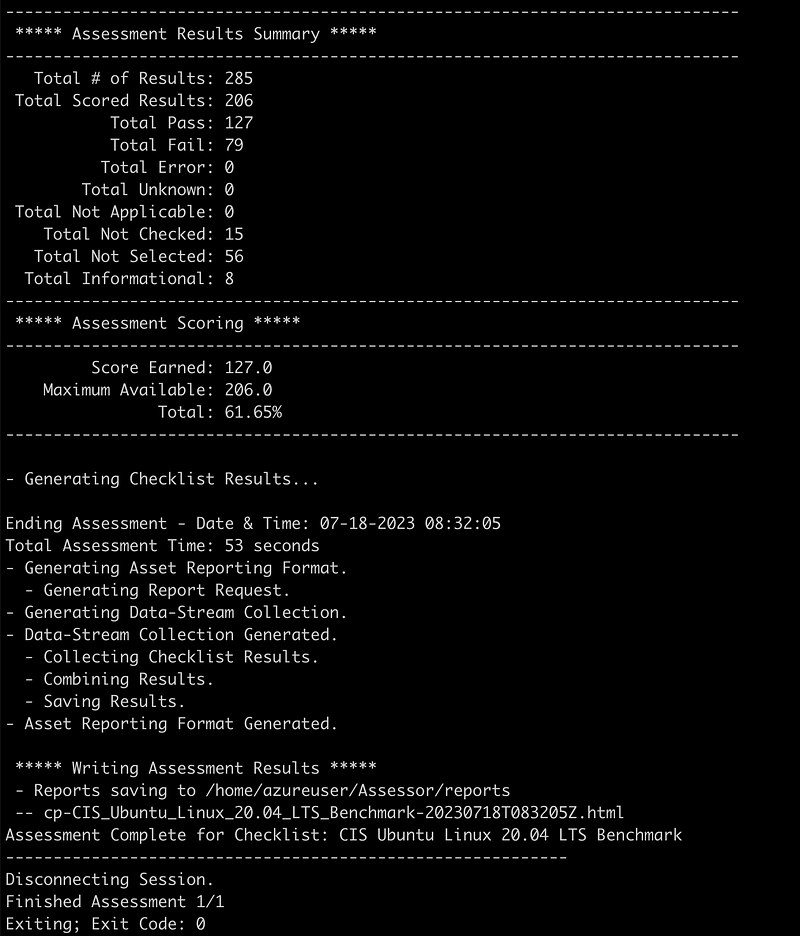
- Copy the listed HTML file to your local machine using scp, sftp, or some other tool. Your information will be different, such as the IP, hostname, and filename.
- Copy the path from the Results output. Use a local browser to examine the file. The example below is split to fit on the page, your path would be continuous.
- And here is the nice report generated by the tool:

Within the report, you will find the detailed list of all the configurations necessary to protect your server and whether they fail or pass.
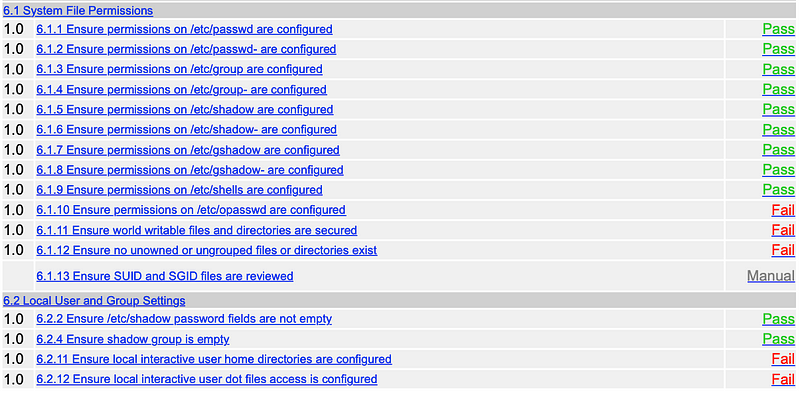
Clicking on a failed check with take you the the details and how to remediate with a working walk through example:

Take away
As cloud computing has become business as usual for many businesses, frequent news reports about data breaches and other missteps should make companies think carefully about how they secure their data.